
Report: Cybercriminal activity around business email compromise surges by 38% in last 3 years
share on
The number of cybercrime-as-a-service targeting business email has surged by 38% between 2019 and 2022 globally, a report by Microsoft finds.
Conducted by Microsoft, the Cyber Signals spotlights security trends and insights gathered from Microsoft’s 43 trillion daily security signals and 8,500 security experts. The report highlights a surge in cybercriminal activity around business email compromise (BEC), the common tactics employed by BEC operators, and how enterprises can defend against these attacks.
Between April 2022 and April 2023, Microsoft Threat Intelligence detected and investigated 35 million BEC attempts with an average of 156,000 attempts daily. It also observed a 38% increase in cybercrime-as-a-service targeting business email between 2019 and 2022. One of such services is BulletProftLink that creates industrial-scale malicious mail campaigns, which sells end-to-end service including templates, hosting, and automated services for BEC.
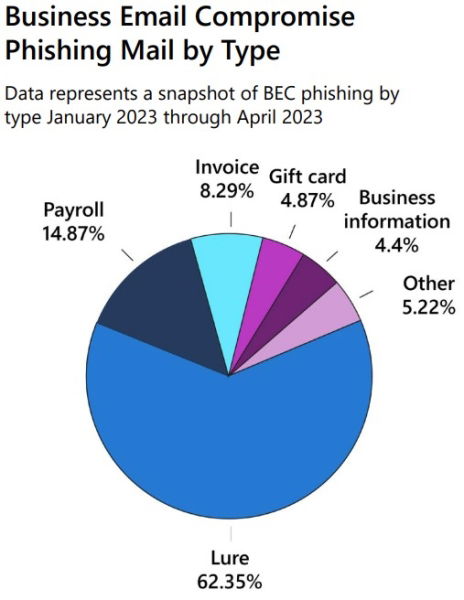
Top targets for BEC are executives and other senior leaders, finance managers, human resources staff with access to employee records such as social security numbers, tax statements and other PII. New employees who are less likely to verify unfamiliar email requests are also targeted. Nearly all forms of BEC attacks are on the rise. Top trends for targeted BEC attacks include lure (62.35%), payroll (14.87%), invoice (8.29%), gift card (4.87%) and business information (4.4%).
Instead of exploiting vulnerabilities in unpatched devices, BEC operators seek to exploit the daily sea of email traffic and other messages to lure victims into providing financial information or taking direct action such as unknowingly sending funds to money mule accounts that help criminals perform fraudulent money transfers. Threat actors’ BEC attempts can take many forms such as phone calls, text messages, emails, or social media outreach.
Don't miss: MINISO Hong Kong says it has no relation to scam website
Microsoft has provided a few suggestions to protect against BEC attacks. Firstly, businesses may leverage cloud apps that utilise AI capabilities to enhance defenses, adding advanced phishing protection and suspicious forwarding detection. Crucially, businesses need to secure identities to prohibit lateral movement by controlling access to apps and data with Zero Trust and automated identity governance.
Furthermore, adopting a secure payment platform can reduce the risk of fraudulent activity by switching from emailed invoices to a system specifically designed to authenticate payments. Additionally, enterprises may educate employees to spot fraudulent and other malicious emails, such as a mismatch in domain and email addresses, and the risk and cost associated with successful BEC attacks.
Vasu Jakkal, corporate vice president, security, compliance, identity, and management at Microsoft, said: “BEC attacks offer a great example of why cyber risk needs to be addressed in a cross-functional way with IT, compliance and cyber risk officers at the table alongside business executives and leaders, finance employees, human resource managers and others with access to employee records. While we must enhance existing defenses through AI capabilities and phishing protection, enterprises also need to train employees to spot warning signs to prevent BEC attacks.”
MARKETING-INTERACTIVE has reached out to Microsoft for more information.
Related articles:
Microsoft's Bing gets a jolt with AI capabilities, but will comfortable consumers actually switch from Google?
FTC plans to block Microsoft’s acquisition of Activision Blizzard
Microsoft Indonesia and Pos Indonesia join hands to accelerate digital transformation
After Tenaga Nasional, Microsoft partners with Digital Penang for transformation
share on
Free newsletter
Get the daily lowdown on Asia's top marketing stories.
We break down the big and messy topics of the day so you're updated on the most important developments in Asia's marketing development – for free.
subscribe now open in new window
